In an era where software security is paramount, Static Application Security Testing (SAST) has emerged as a critical tool in the developer toolkit and an increasingly vital component of DevSecOps. Through meticulous inspection of software artifacts, SAST enables developer teams and security professionals to spot vulnerabilities early in the development cycle.
In this article, we explore SAST, diving into what it really means and how it contributes to a more robust and secure software development life cycle (SDLC). Read on to discover why and how organizations, including Sonatype, integrate SAST as a key part of their DevSecOps strategies.
SAST definition
Static Application Security Testing, commonly referred to as SAST, is a testing methodology that scrutinizes source code, bytecode, or application binaries for vulnerabilities without executing the underlying program. Simply put, it is a "white box" approach to identifying security flaws in applications, examining application code statically (without running it) to find potential security threats.
Why is SAST important?
As part of the modern software development life cycle (SDLC), ensuring an application's security is as vital as its functionality. SAST helps developer teams do this in several ways:
-
Shifting Left: By integrating SAST into the SDLC, teams can detect vulnerabilities early, (known as Shift Left or Start Left) substantially reducing the cost and effort of late-stage remediation.
-
Thorough examination: SAST tools provide a deep dive into your source code, identifying patterns that might pose a security threat.
-
Empower developers: Just as DevSecOps has made developers integral to security, SAST provides them with the tools to produce secure code from the outset.
-
Comprehensive security: With both SAST and other tools in place, teams can achieve a holistic security posture, safeguarding not just the application but the entire software ecosystem.
How does SAST Work?
Instead of evaluating the software's external behavior, as some testing approaches do, SAST scrutinizes the application's source code, bytecode, or binaries without needing to execute the program. Through SAST scanning and specific algorithms, these tools identify patterns and code snippets that might contain vulnerabilities or insecure coding practices.
As a result, potential security threats such as SQL injections, buffer overflows, or cross-site scripting can be flagged early in the development phase. This means SAST occurs before the code is even run, offering developers immediate, actionable feedback on potential issues.
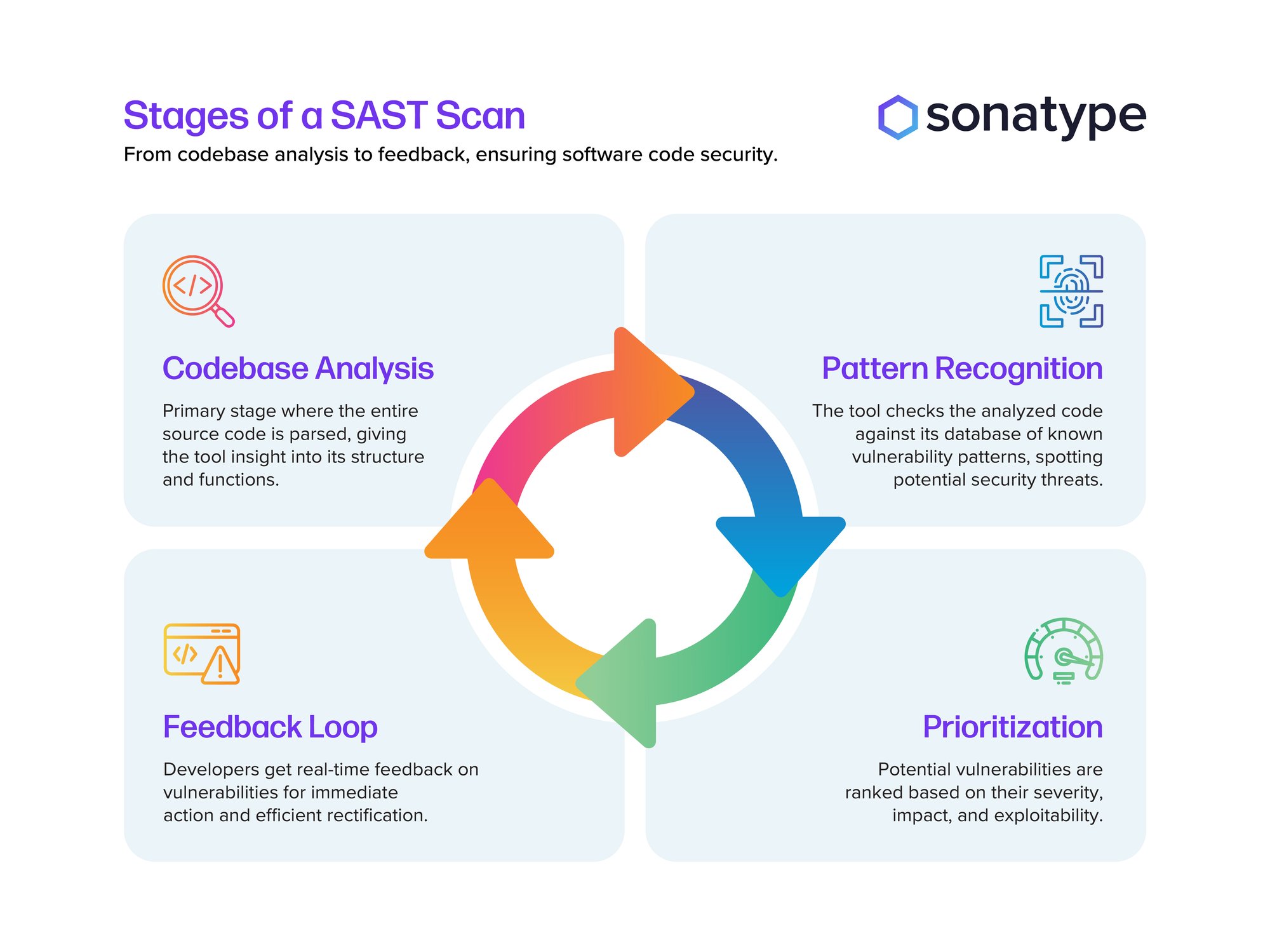
Stages of a SAST scan
A SAST scan generally follows a structured progression to thoroughly examine and ensure the security of software code. Here's an overview of the typical stages of a SAST scan:
-
Codebase analysis: At this primary stage, the entire source code of the application is parsed, enabling the tool to understand its structure and functionalities.
-
Pattern recognition: Armed with a comprehensive database of known vulnerability patterns, the tool scans the analyzed code to identify any matching patterns or potential security threats.
-
Prioritization: After identifying potential vulnerabilities, they are ranked or prioritized based on their severity, potential impact, and the ease with which they can be exploited.
-
Feedback loop: In real-time, developers are provided with feedback on the detected vulnerabilities. This ensures immediate action can be taken, allowing for faster and more efficient rectification.
Benefits of SAST
Software Application Security Testing (SAST) has become an integral component of modern software development practices, offering numerous advantages that ensure a more secure and efficient development process. Here are the benefits of incorporating SAST into your development lifecycle:
-
Proactive security: One of the standout benefits of SAST is its ability to identify vulnerabilities even before the software runs for the first time. This preemptive approach means that potential security threats are caught and rectified well in advance.
-
Ensuring secure coding: By integrating SAST tools, organizations can ensure that their developers adhere to secure coding standards and best practice. This not only enhances security posture but also educates developers on security norms.
-
Detects common vulnerabilities: SAST tools are equipped to identify a wide range of common vulnerabilities, such as SQL injection, cross-site scripting, and buffer overflows, among others. This comprehensive detection ability ensures that software is guarded against prevalent threats.
-
Detailed insights: Rather than just flagging vulnerabilities, SAST tools support developers by actively explaining the risks. They highlight specific sections of problematic code and offer insights into why a particular snippet might be vulnerable as well as providing suggestions for rectification.
-
Early detection: Identifying and addressing security issues during the development stage dramatically reduces the costs and efforts of remediation - it's always more time-consuming and expensive to fix vulnerabilities post-production.
-
Versatility: Modern SAST solutions are designed to be adaptable. They can cater to a variety of coding languages, frameworks, and environments, ensuring a broad scope of application and compatibility.
-
Speed: In an agile development environment, speed is paramount. SAST tools can provide almost instantaneous feedback, ensuring that the development process remains swift, while not compromising on security.
SAST limitations
While SAST offers a plethora of benefits to software development, it's important to remember that no tool or approach is without its limitations. When evaluating the role of SAST in your SDLC, consider the following challenges and constraints:
-
False positives/negatives: One of the common challenges faced with SAST is the occurrence of false positives, where the tool might flag code as vulnerable when it's not. Conversely, false negatives are instances where actual vulnerabilities are overlooked. These can sometimes lead to unnecessary work or overlooked risks.
-
Language dependency: Not all SAST tools are universal. Some might cater specifically to certain programming languages, which can be a limitation if your application uses multiple languages or a less common one.
-
Contextual limitations: SAST tools analyze static code, meaning they might miss vulnerabilities that manifest only in a specific runtime environment or require user interaction.
-
Rapid obsolescence: The world of cyber threats is ever-evolving. While SAST tools are updated regularly, there's always a lag between the emergence of a new threat and the tool's ability to detect it. Regular updates and tool calibration are crucial.
-
Dynamic environment limitation: Some vulnerabilities become evident only when the application is running. SAST, being a static analysis tool, might not catch these, underscoring the importance of also having dynamic testing tools in place.
SAST vs. other AppSec tools
SAST software is just one tool in the toolbox for effective application security, with plenty of other methods existing to help developers identify and mitigate vulnerabilities. So, how do SAST tools compare to other options in the AppSec arsenal?
SAST (Software Application Security Testing): This tool is all about preventing vulnerabilities at the earliest stage. By examining the codebase without running the application, SAST can spot potential threats before they become real issues in the execution phase.
DAST (Dynamic Application Security Testing): As the name suggests, DAST is dynamic. It probes running applications for potential vulnerabilities, simulating real-world attack scenarios. This means DAST can find vulnerabilities that only manifest during operation, giving a clear picture of threats in a live environment.
IAST (Interactive Application Security Testing): IAST combines aspects of SAST and DAST, capturing information in real time as the application runs. By leveraging both static and dynamic analysis, IAST can offer deep, comprehensive insights into application security.
SCA (Software Composition Analysis): Modern applications often rely heavily on open source and third-party components and libraries. While these speed up development, they can introduce vulnerabilities. Software Composition Analysis focuses on identifying vulnerabilities in open source or third-party software dependencies, ensuring that the external components your application relies on remain secure. This vigilance in analyzing components is essential for maintaining the integrity of the software supply chain, as each external piece integrated into your application could potentially be a point of compromise.
While each tool offers unique advantages, relying on just one can leave blind spots in your security posture. The most robust application security approach is a multi-faceted one, harnessing the strengths of SAST, DAST, IAST, and SCA for a truly holistic view of vulnerabilities and threats.
How frequently should you do code scanning and security assessment?
In the ever-evolving landscape of cybersecurity, consistent vigilance is more than just a best practice - it's a necessity. Static Application Security Testing (SAST) offers a proactive approach to mitigating potential vulnerabilities in your application. But how often should you be employing SAST scans?
The answer is: as regularly as possible! With new threats emerging daily and codebases being continually updated, infrequent SAST scanning can lead to overlooked vulnerabilities. As developers push updates, introduce new features, or refactor code, the potential for introducing a security flaw inadvertently increases.
With the dynamic nature of security threats, periodic SAST scanning is crucial. As development teams often push code updates to their source code repositories, integrating SAST into your Continuous Integration/Continuous Deployment (CI/CD) pipeline ensures every code commit in the repository is scrutinized. This means that every time a developer makes a commit or a change to the codebase, a SAST scan is automatically triggered. By weaving SAST into the fabric of your software development life cycle (SDLC), you're not only bolstering security but also fostering a culture where security and development go hand in hand.
So, regular SAST scans are vital to ensuring that your application remains secure amidst constant changes and threats. By making SAST scanning a consistent and integrated part of your development process, you can maintain a strong security posture without impeding the pace of innovation.
Frequently asked questions
In which phase of the SDLC should I use SAST?
Software Application Security Testing (SAST) is most effectively integrated early in the software development life cycle (SDLC). By introducing it during the coding and integration phases, developers can identify and rectify vulnerabilities before they progress further, saving time and ensuring more secure code. By introducing it during the coding (as developers commit to the source code repository) and integration phases, vulnerabilities can be identified and rectified more efficiently.
When does static application security require access to source code?
SAST isn't just limited to analyzing raw source code. It requires access to either the source code, bytecode, or application binaries to perform a thorough and accurate analysis, ensuring potential vulnerabilities are identified and mitigated.
Which type of security assessment requires access to source code?
When it comes to analyzing and detecting vulnerabilities directly from the raw materials of an application, SAST stands out. SAST necessitates access to the source code, enabling a deep dive into potential security issues at the code level.
What vulnerabilities can SAST tools find?
SAST tools are equipped to detect a wide array of vulnerabilities within an application's code. This encompasses issues like SQL injections, cross-site scripting (XSS), insecure data handling practices, buffer overflows, and many other potential security threats that might lurk in the code.
%3F&_biz_n=0&rnd=118613&cdn_o=a&_biz_z=1745590815238)
%3F&rnd=884323&cdn_o=a&_biz_z=1745590815240)