I get asked often what Sonatype's automated malware detection system, Release Integrity, has found so far. Great question.
Back in 2019, Sonatype announced the release of its new technology with early warning capabilities to find malicious releases of open source components, known as "counterfeit components." Release Integrity is part of next-gen Sonatype Intelligence, detecting and blocking their use within modern software factories. We knew then that the future of open source security was changing - and the past year shows just how right we were.
Since then, this technology has time and time again identified novel malware -- including those missed by leading antivirus engines, lurking in open source components. With it, Sonatype was the first and only company to proactively catch the dependency or namespace confusion PoC research packages from Alex Birsan when they first sprung up in 2020.
Using automated malware detection systems, the service flagged Birsan's packages in early 2020 as malware. At the time, the researcher told Sonatype that this was part of ongoing research work and that a coordinated disclosure would take place in early 2021. This vulnerability was revealed as promised, affecting more than 35 organizations, including major software companies like Microsoft, Uber, Tesla, Yelp, and Shopify.
Since then, the Sonatype Security Research Team has repeatedly added these packages to our data under multiple vulnerability identifiers (sonatype-2020-XXXX IDs), keeping our customers protected from the get-go.
At publish date, we have identified upwards of 12,000 suspicious and malicious npm packages.
This figure includes packages infiltrating npm that emerged this year, including:
-
Novel malware, typosquatting, and brandjacking
-
Hundreds of original dependency confusion PoCs
-
Thousands of dependency hijacking copycats, malicious and otherwise
-
Bug bounties and contributions by security researchers and infosec activists
Today we roundup popular malware that Sonatype's Release Integrity has identified thus far, which is by no means an exhaustive list:
1. Web-browserify
In April of this year, Sonatype's Release Integrity spotted a rather unique macOS and Linux malware sample published to the npm registry, targeting developers. Existing in the brandjacking npm package "web-browserify," the malware imitated the legitimate "browserify" component that receives over 1.3 million weekly downloads on npm alone.
Of note is that the package seems to be specifically designed to target individual NodeJS developers, judging from the way it acts once downloaded, as well as the choice of operating systems that it targets.
2. Malware named after popular company repos
In March, we first identified malicious dependency confusion packages that were named after repositories, namespaces, or components used by companies such as Amazon, Zillow, Lyft, and Slack.
These packages were called:
-
amzn
-
zg-rentals
-
lyft-dataset-sdk
-
serverless-slack-app
Thanks to Sonatype's timely report to npm, these packages were nuked before they caused harm to anyone.
3. 5,000+ vigilante activism packages flood npm and PyPI
Earlier this year and shortly after dependency confusion news broke, entities began flooding npm and PyPI with copycat packages. While most of these packages were PoC research ones by prospective bug bounty hunters, some were malicious.
And yet another breed of these copycats caught by Sonatype included those that spread awareness about supply-chain attacks:

Image: Example supply chain attack reminder packages on npm
In total, Sonatype's Release Integrity spotted 1,500+ dependency confusion npm packages posted by a vigilante actor to spread awareness about risks of supply chain attacks. Combined with 3,600+ similar packages that flooded PyPI at the time, the total count of identified dependency confusion copycats was over 5,000.

Image: Dependency Confusions Packages above a given threshold per day
Sonatype had been persistently catching dependency confusion packages months before the news broke. At the time, we were told that these packages were part of ethical research and that a coordinated disclosure with the vendor was pending.
Fortunately, I was the first person to break the news story on BleepingComputer after working with Birsan, who released his detailed findings at the same time.
Within just 48 hours of the dependency hijacking method becoming news, Sonatype saw a sharp uptick in Release Integrity's newly caught copycat packages, as more and more researchers began hunting for bug bounties by trying to use this method.
4. Malware containing njRAT/Bladabindi trojan
Over the Thanksgiving weekend in 2020, Sonatype discovered another novel malware within the npm registry. This time, the typosquatting packages were laced with a popular Remote Access Trojan (RAT).
The malicious packages were:
- jdb.js
- db-json.js
These mimicked the legitimate NodeJS-based database libraries, including jdb and db-json, but downloaded the malicious njRAT aka Bladabindi onto the user's system.

Image: hardcoded strings within patch.exe sample, such as C2 server IP address, name of the dropped process, etc.
Our blog post from last year details what these packages did and their capabilities. Thankfully, these were caught by Sonatype just before they could cause havoc on developers' software supply-chains.
5. CursedGrabber malware campaign
November 2020, Sonatype spotted a whole new family of Discord-stealing malware written in C#. Threat actors had uploaded packages such as "xpc.js" to npm as typosquatting and brandjacking packages, with many similar uploads following afterwards.
Our report on the CursedGrabber family, as analyzed by Sonatype security researcher Sebastián Castro, details the extensive capabilities built into this Discord stealer. The attack even attempted to retrieve and exfiltrate user's payment and billing information from their Discord account, in addition to their tokens and other sensitive data:

Image: Lib.exe retrieving payment information in addition to Discord tokens and web browser files
At the time of our discovery, CursedGrabber variants had either a low or zero detection rate on VirusTotal.
Following Sonatype's analysis, antivirus engines and threat intel platforms began catching up and adding CursedGrabber's Indicators of Compromise (IOCs) to their data.
6. Successor to "Fallguys" malware
In September 2020, ZDNet had reported on malware pretending to be a video game's API. The malicious component "fallguys" lived on npm downloads impersonating an API for the widely popular video game Fall Guys: Ultimate Knockout. Its actual purpose however was rather sinister.

Image: Fall Guys Ultimate Knockout game (under Fair Use)
Two months later, Sonatype's Release Integrity system caught multiple components that succeeded the Fallguys malware. Including discord.dll, discord.app, wsbd.js, and ac-addon, they were named for legitimate components, but were brandjacking packages touted as Discord-related plugins.

Image: Contents of the obfuscated code
Deobfuscating and reformatting the code revealed references to Discord, webhooks, setting and getting cookies, "sending" data, Discord tokens, and web browser files.
Our complete report on this campaign elaborates on the technical findings.
7. "Twilio-npm"
As if the increasing attacks on the open source ecosystem and vulnerabilities making headlines weren't scary enough, last year's Halloween exposed devs to another malicious trick.
Yes, we are referring to the malicious npm package described in last year's report.
The official twilio npm package gets downloaded close to half-a-million times weekly, making its popularity a target for threat actors. This identically-named "twilio-npm" counterfeit component tricked Twilio developers with a single-file malware that spawned a reverse shell on the developer's system as soon as it was caught.
Image: twilio-npm file
Thanks to Sonatype's report to npm, the malware was taken down in time to keep Twilio's users and developers around the world safe.
8. Electorn
Finally, the package that started it all: the misspelled "electorn" package was Sonatype's first newsworthy finding from Release Integrity. The program targeted developers seeking the legitimate and hugely popular Electron library via typosquatting.
As described in an earlier blog post, the malicious "electorn" package, along with some others we flagged, exfiltrated user's IP address, country, city, and a base64-encoded device fingerprint. The information contained included the logged in user, their home directory, and their CPU. When decoded, it would appear for example as:
johnsmith/Users/johnsmithIntel(R)Core(TM)i5-XXXXXCPU@2.30GHz
Soon after its installation, this information was uploaded every few minutes to a public GitHub page that was visible to all.

Image: Example exfiltrated data (details redacted)
But with Sonatype's timely discovery and reporting of these malicious typosquats, harm to developers' information and their software supply chains was averted.
Thousands of components spotted thus far, and counting
These are just a few examples of suspicious components that Release Integrity has flagged thus far, and will continue to flag.
You can meet the developers behind our automated malware detection system that continues to add enhancements and improvements, helping keep everyone's software supply chains safe!
A discussion with two of these developers is also available, including principal software engineer Xiaorong Xiang and data scientist Cody Nash, where they explain the analysis behind every newly published npm package. They detail how the software is ingested and evaluated by the Release Integrity system against over five dozen "signals" or red flags that indicate a suspicious package.
For example, criteria includes package age, the author's whereabouts, and more importantly, the code inside the package.
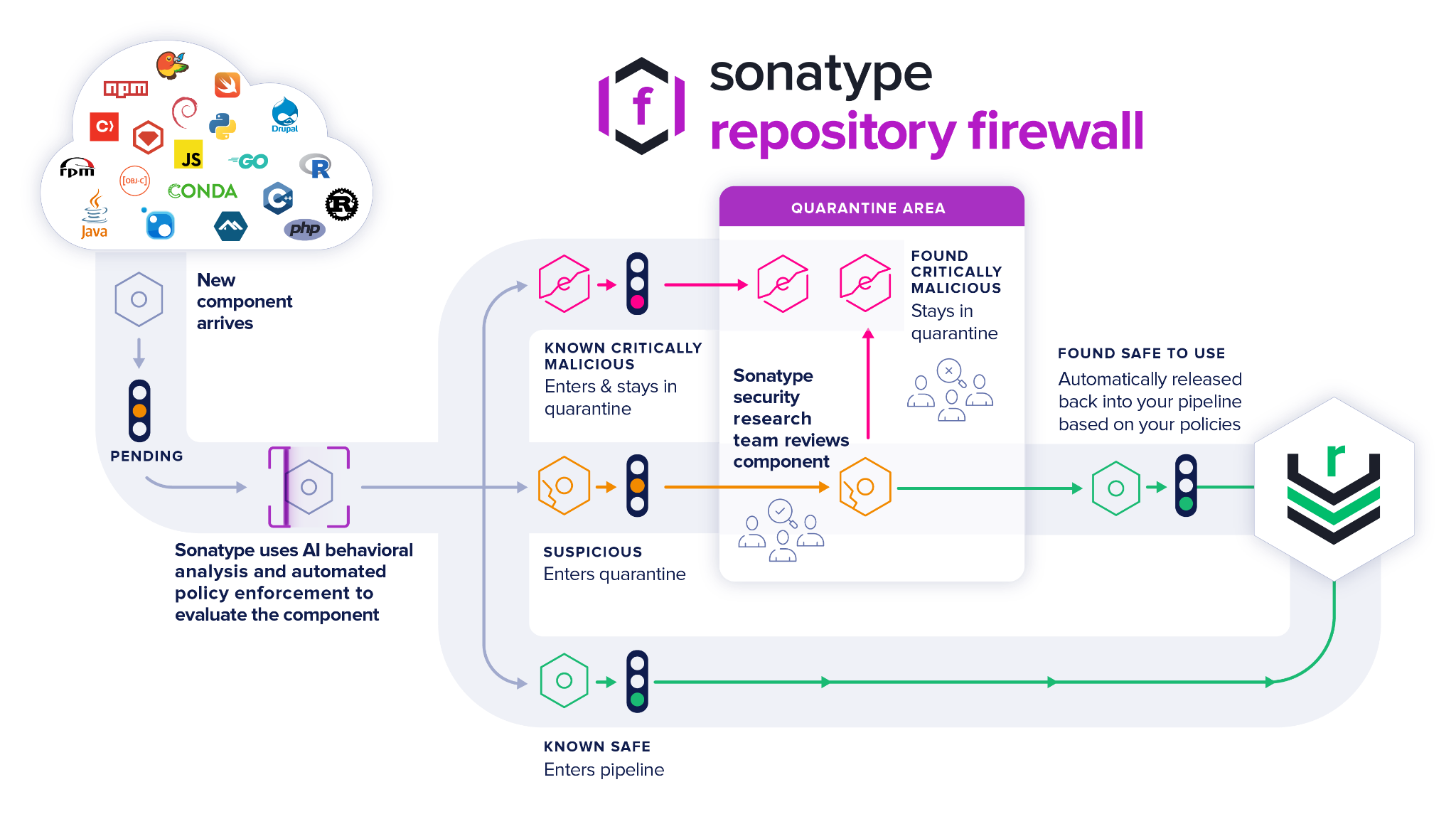
Image: Release Integrity flowchart
As soon as Release Integrity flags a package or a dependency as "suspicious," it undergoes a quarantine queue for manual review by the Sonatype Security Research Team. Meanwhile, users of Sonatype Repository Firewall will be protected from these suspicious packages while the manual analysis is underway. Existing components will be quarantined before they are pulled "downstream" into a developer’s open source build environment.
Moreover, users with the "Dependency Confusion Policy" feature configured will get proactive protection from dependency confusion attacks, should conflicting package names exist in a public repository and their private, internal repos.
Users of Sonatype Nexus Repository can additionally download Sonatype's "dependency/namespace confusion checker" script from GitHub to determine if they have artifacts with the same name between repositories. It will also determine if they have been impacted by a dependency confusion attack in the past. Routing rules can also be enabled to dictate that internal dependencies are pulled from a trusted repository.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.

Ax is a Staff Security Researcher & Malware Analyst at Sonatype with a penchant for open source software. His works and expert analyses have frequently been featured by leading media outlets including the BBC. Ax's expertise lies in security vulnerability research, reverse engineering, and ...
Explore All Posts by Ax Sharma


