Recently, I played with Docker Swarm and decided to set up a containerized Sonatype Nexus Repository as my Docker registry.
But to be able to work as a Docker registry, you need to use HTTPS. I found lots of articles about using Sonatype Nexus Repository as a Docker registry, but not a containerized Sonatype Nexus Repository. That's what I'm going to describe. A solution is to use a proxy, let it handle the security, and use plain HTTP between the proxy and Sonatype Nexus Repository, but that's not what I'm interested in.
Install Dockerized Sonatype Nexus Repository
That part is the easiest one.
Although it's not the recommended way to do it, I'm going to use a mounted volume. I find it easier to manipulate what's inside that way.
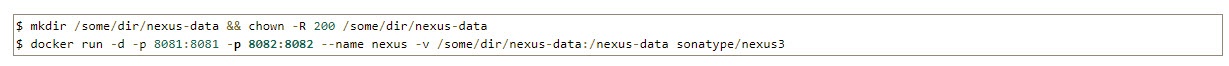
Note that, despite the command line in the doc, we are opening two ports, since we need another one for HTTPS. Choose it carefully, as it will be used after.
Source: https://github.com/sonatype/docker-nexus3
Once you start Sonatype Nexus Repository, you can see the /some/dir/nexus-data directory growing.
Content of nexus-data:
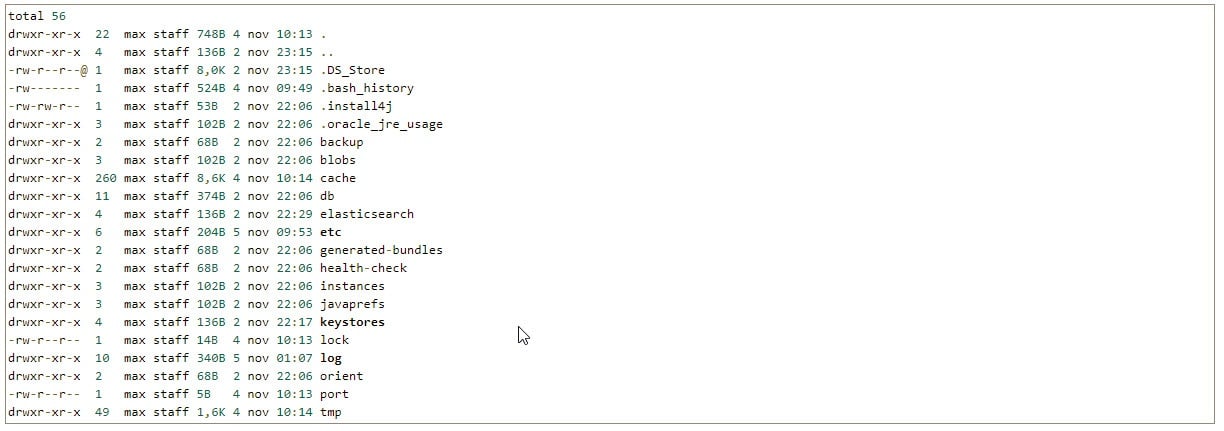
The three directories in bold are the ones we will use next.
Adding a Valid Name for Our Certificate
In real life, your certificate should match the DNS or machine on which you're hosting Sonatype Nexus Repository.
But in my case, it's just a local environment for testing purposes.
So I just added a value in /etc/hosts

Creating Java KeyStore
As Jetty is the underlying web container, a Java KeyStore (JKS) is needed to contain your certificate. Here, we will use a CSR.
First, go to the directory /some/dir/nexus-data/keystores and then create your CSR.

Updating the Configuration: jetty-https.xml
Since the Dockerized image of Sonatype Nexus Repository exposes only the directory /nexus-data through a volume, we don't have access to the HTTPS configuration, which is located in /opt/sonatype/nexus/etc/jetty/jetty-https.xml.
To do so, let's create a writable Jetty configuration directory.

Then start your Dockerized Sonatype Nexus Repository and launch a bash prompt.

Once in the container, copy the file jetty-https.xml so it's accessible from the host and not deleted every time we relaunch the container.

Edit the file jetty-https.xml and modify the section accordingly:
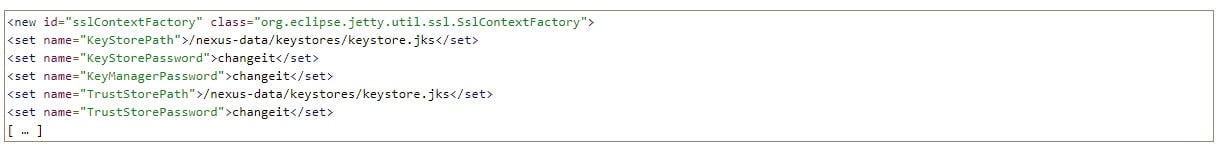
As you can see, we deleted the property name « ssl.etc » since it tells Jetty to look for the path under /etc/ssl, which is a directory we cannot modify within the container.
nexus.properties
Then edit the file /some/dir/nexus-data/etc/nexus.properties to uncomment the line enabling the HTTPS port, and write the value you defined when you created your container.

Uncomment and modify the line, allowing to tweak jetty configuration.
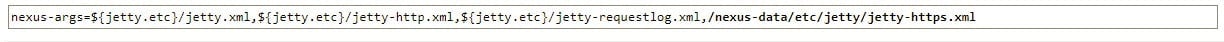
Then restart your container and tail the log.

You should observe the correct opening of both HTTP and HTTPS ports.
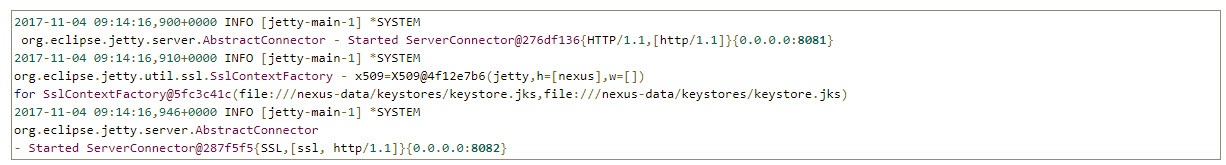
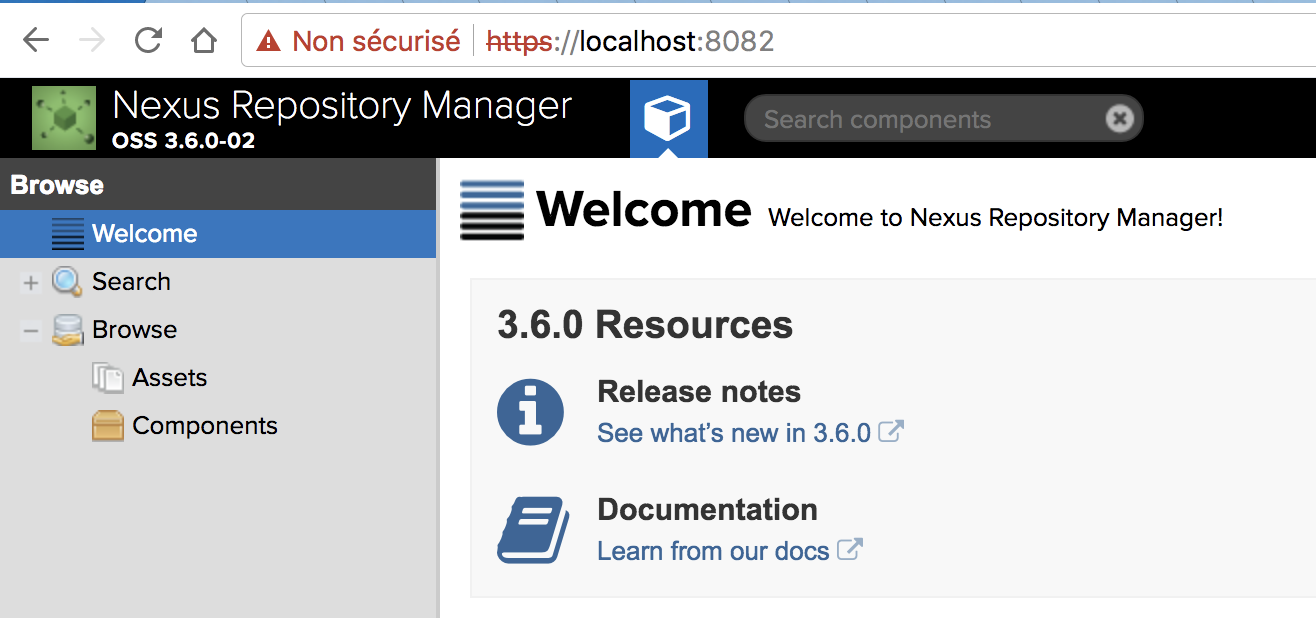
Our certificate is self-signed, so it is considered not valid by the browser.
Configure Docker Daemon to Trust the Certificate
You'll now have to configure the docker daemon to trust your certificate.
I'm not going to describe something that has already been. Just look at the description at the end of this article and you're good to go.
This article was originally published Maxence Button on Marence's Technical Corner
Written by Maxence Button
Tags

Try Nexus Repository Free Today
Sonatype Nexus Repository is the world’s most trusted artifact repository manager. Experience the difference and download Community Edition for free.