Nexus Lifecycle is our automated solution for preventing security breaches like the one that impacted Equifax this past week. Thanks to our IDE integration, remediating these issues is very straightforward.
Detection and remediation can also be accessed from Nexus Repository Manager 3.1 (or later) using the step-by-step documenation below. If you don’t have Lifecycle or Nexus 3.1, never fear. Our stand-alone tool, Application Health Check (AHC), is a free service we provide to help you see if a particular application is affected by vulnerabilities.
In this step-by-step documentation, we'll show how to utilize AHC from within Nexus 3.1.
Step-by-Step walk through of vulnerable component detection with Nexus 3.1
Start by opening Nexus Repository in a web browser.

In the search field, type the name of an application you develop that depends on the struts2-rest-plugin component (and is hosted in Nexus Repository). In our case, we’ll just search for the plugin directly.

From the search results, choose the component you’re interested in.

The component detail page gives you additional information about the component, including the repository it comes from, how old it is, and popularity information. However, we’re interested in the Application Health Check features, so we click the Analyze application button.

In order to get a summary report, we need to provide an email and a password to unlock the report, then click Analyze to start the process.
After a few minutes, an email like the following will show up in your inbox.

Click the summary report here link to access the report. Use the email and password you provided earlier to unlock the report.


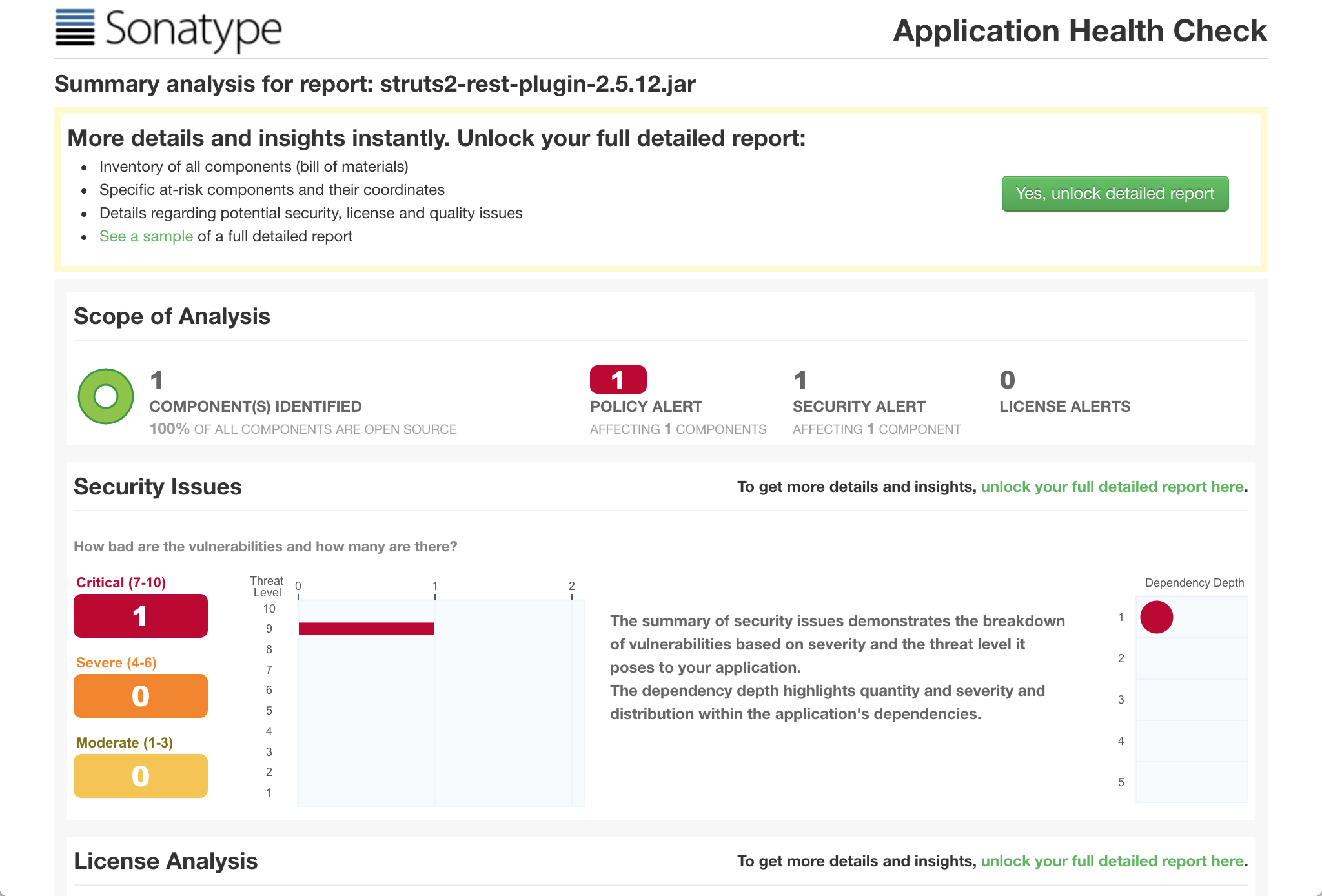
There’s clearly a problem with this component. To see more details, click the Yes, unlock detailed report button.

Once you provide us with a little more information about yourself, click the Receive Detailed Report button.
After a few minutes, the following email will show up in your inbox.

Click the link in the email to open your detailed report.

Once you open the report, you might notice a few additional tabs at the top of the report. Click the Security Issues tab to see more information about the critical vulnerability shown in the summary.

As you see, CVE-2017-9805 is responsible for the issues with this component. Click it to see more detail.

In the popup that appears, we give a description from the CVE, as well as our own explanation and recommendation for fixing the problem.
So yes, there are a few more hoops to jump through if you’re an OSS user, but thanks to the Application Health Check, you can still access the data that powers our automated Nexus Lifecycle solution.
Video - Step by Step
You can view the entire step-by-step process in this 4 minute video.
Conclusion
You can find out in less that five minutes if your applications are using vulnerable components like Struts2. It's free. It's fast. It's available right now.
Download links:
- Application Health Check stand-alone tool (free)
- Application Health Check within Nexus 3.1 (free)
- Nexus Lifecycle: Automated Enterprise Monitoring and Notification

Written by Daniel Sauble
Daniel is a Product Owner at Sonatype. He enjoys building software tools for developers and sysadmins and has spent the last eight years in DevOps startups. He has experience in Product Management, UX Design, User Research, Software Development, and Data Science.