If you had a heart attack, would you stop eating cheeseburgers? For most people, the answer is “No”. A recent survey of 1,000 survivors found that 60 percent of heart attack victims weren't sticking to a healthy diet and about 30 percent still had high cholesterol and blood pressure. Hey, old habits (especially the tasty ones) die hard.
Funny thing is, the same behavior for those who have suffered a heart attack is found in application security. If you have been breached, chances are you have not changed your security diet.
The Bulk of Breaches
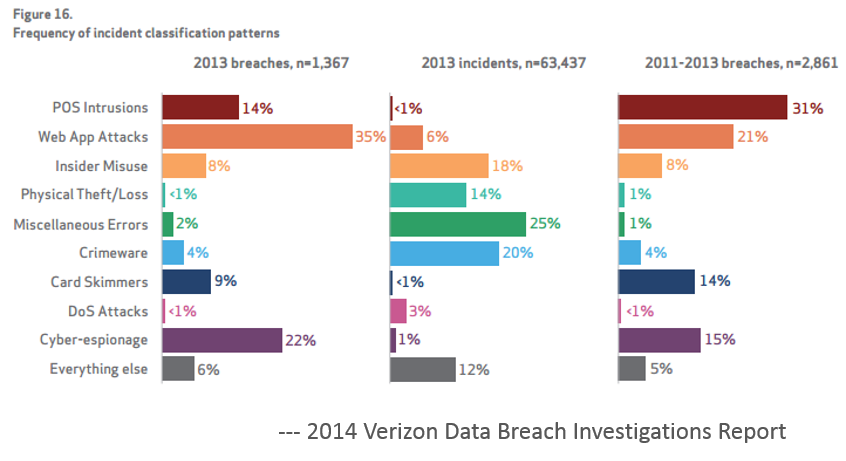
In April’s release of the 2014 Verizon Breach Investigations Report, applications were shown as the number one attack vector leading to breaches. According to the report, applications account for more breaches than cyber-espionage, insider misuse, crimeware, and DoS attacks combined.
Yet, given this known risk, we continue to focus our security priorities elsewhere. A few weeks ago, in a webinar entitled “Lessons Learned from Heartbleed, Struts, and the Neglected 90%” featuring Joshua Corman (CTO at Sonatype) and Wendy Nather (Security Research Director at 451 Research), both shared remarks about how we are spending the least amount of time and energy on the most attacked vector within our infrastructure.
If you are an application hacker, this is great news! Your targets, even if breached, are not likely going to change their behavior or refocus their priorities. You can almost hear them placing the order…“more cheeseburgers, please”. On the other hand, the customers these applications serve may feel differently.
Oh, Boy.
Speaking of customers, there was another interesting data point shared in the Verizon report: for financially motivated application attacks, can you guess the best source organizations had for determining if they had experienced a breach? Internal IT Audits? Nope. External monitoring services? Guess again. Internal fraud detection? Sorry. Seventy-four percent (74%) of the time, it was: THE CUSTOMER. Oh, boy. If your best application security defense is your customer, something is wrong here. Very wrong.
Yes Sir, May I Have Another
No doubt, companies spend lots of time and energy on security. The problem is, the inertia of today’s activities are focused on the old attack points: network, data, and host security. In his recent tweet, @JoshCorman shared, “People don’t change until the pain of maintaining inertia exceeds the pain of change”.
Which brings me back to cheeseburgers. During an April briefing with Wendy Nather of 451 Research, we discussed something she calls “cheeseburger risk.” According to Wendy, “Cheeseburger risk is the kind of risk you deliberately take even knowing the consequences, until those consequences actually come to pass. For example, you may decide to go on eating cheeseburgers until such time as you have a heart attack – and then you’ll consider changing to a healthier lifestyle.”
“You can calculate the probability of something bad happening in security, and present it to your executives”, she continued, “But no matter what scoring system you use, they may choose not to do anything until the probability equals 1. I’ve heard real quotes from security professionals that they’ve gotten from customers, such as, ‘Let’s wait until we actually get attacked.’” (You can read more on Wendy’s cheeseburger perspective here).
“Doc, It Hurts When I Do This”
Verizon’s report tells us that applications are your most likely attack vector for a breach. They are where your heart attacks have occurred or are most likely to occur next. While doctors might tell you to balance your diet (or in this case, your security priorities), for now it looks like most organizations are ignoring the advice. Even when we’ve heard the next heart attack – or heartbleed – is around the corner, we just hope it’s not our own.
If you have any say in your company’s security priorities, I encourage you to share this perspective with your colleagues. Have a lunchtime discussion about the state of your application security health – perhaps over a couple of cheeseburgers.
Regardless of the outcome, you will certainly benefit from the discussions. And if it turns out that you’re not that keen on changing your diet to prevent that next attack, perhaps you’ll be motivated to do it for your children’s sake…sorry, I meant your customer’s.
Cheeseburger image source: http://dailyoftheday.com/wp-content/uploads/2012/09/unknown-cheeseburger.jpg

Written by Derek Weeks
Derek serves as vice president and DevOps advocate at Sonatype and is the co-founder of All Day DevOps -- an online community of 65,000 IT professionals.
Explore All Posts by Derek WeeksTags



