
The (ISC)2 Global Information Workforce Study CXO Report was recently released. The report found some interesting and troubling data on application security. While security executives noted that application vulnerabilities were their top concern, this did not translate into how their security team invested their time - in fact, focusing on software development was at the bottom of their list.
Application vulnerabilities is the top concern of security executives:
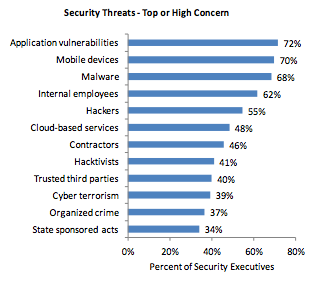 Top Security Threats - Source: (ISC)² Global Information Security Workforce Study
Top Security Threats - Source: (ISC)² Global Information Security Workforce Study
Then report states… "Adding to the potential for disruptions is the on-going feature and functionality race, frequently accomplished without a full understanding of the security risks. Security, consequently, is an after the-fact consideration in application development. Yet, bringing security into the forefront of application development is a costly anchor in this feature and functionality race."
Organizations are not devoting time and spend to application security:
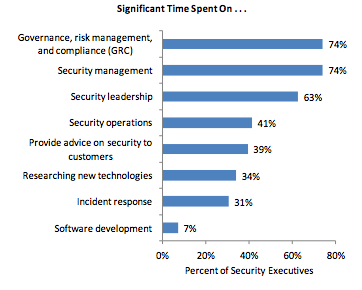 Security Related Activities - Source: (ISC)² Global Information Security Workforce Study
Security Related Activities - Source: (ISC)² Global Information Security Workforce Study
The report states… "A missing element in security executive attention and spending is proactively addressing application vulnerabilities. However, in the chart showing where security executives are spending their time, software development was the lowest (only seven percent of security executives stated they spend significant time on software development). A similar result was found with the rank-and file—time spent on secure software development is a low priority activity; and certifications in secure software development is also low relative to other types of security certification."
Why is this?
- The report notes that the disparity could be due to the fact that organizations mitigate application risk reactively - they may wait until an exploit is occurring, rather than ensuring the code is free from vulnerabilities before it is placed in operation.
- The report also states that security executives feel they have too few security personnel - a total of 63 percent of security executives in private industry and 77% in government. They noted that, "Business conditions were cited as the number one restraint in hiring more security personnel (chosen by 61 percent of security executives)."
So what can be done?
There are many ways to address this problem, but it's unlikely that a huge increase in budget is the answer. Organizations need to expand security coverage without requiring a significant increase in security resources. From an application perspective, the best way to do this is to get the application developers more involved. While training is one way to do this, using an automated policy approach that is designed for agile, component-based development is also important. Using policies to provide guidance to developers early in the process and using policies to enforce action late in the development lifecycle. This provides the flexibility that the developers need to meet their development deadlines, while ensuring that vulnerable code is not deployed to production.
It's a little bit like the DevOps challenge - organizations are expected to develop more applications faster, deploy them more quickly and deploy them more frequently. They are expected to manage larger and more complex systems, and to determine the best mix of on-premise vs. cloud deployments. While expected to do more, they are not receiving additional human resources to accomplish the work. So, what do they do? They turn to automation, they turn to Continuous Integration and Continuous Delivery technologies.
The security team needs to do the same, and they need to make sure the automation is integrated directly into the development lifecycle - or they will just run into more developer resistance.

Written by Derek Weeks
Derek serves as vice president and DevOps advocate at Sonatype and is the co-founder of All Day DevOps -- an online community of 65,000 IT professionals.
Explore All Posts by Derek Weeks