Decrypting the Ledger connect-kit Compromise: A Deep Dive into the Crypto Drainer Attack
4 minute read time
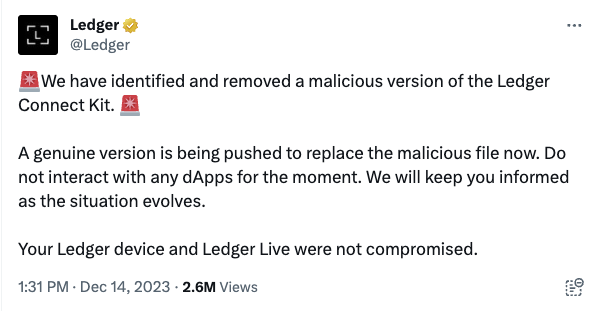
Earlier today, Ledger, a maker of hardware wallets for crypto, announced they had identified malicious software embedded in one of their open source packages called @ledgerhq/connect-kit. This package is widely used as a connector between distributed blockchain applications and crypto wallets that back them up. This analysis focuses on the specifics of the versions 1.1.5 to 1.1.7 compromise, cataloged in our data under sonatype-2023-4890.
Sonatype customers using Sonatype Repository Firewall and Sonatype Lifecycle are protected from this issue. Sonatype security research conducted a deep dive analysis into the issue as it surfaced.
Ledger have since published a complete timeline of the issue on their Twitter account.
Overview of the Incident
The compromised versions of @ledgerhq/connect-kit are 1.1.5, 1.1.6, and 1.1.7. These versions are embedded in numerous crypto applications, from Ledger's own connect-kit-loader to others like Revoke.cash. A critical aspect of this attack is the extensive dependency chain affected. The connect-kit-loader package is a dependency for over 20,454 GitHub repositories, indicating a broad attack surface.
https://twitter.com/Ledger/status/1735291427100455293
Details of the Compromise
An employee of Ledger fell victim to a phishing attack. Attackers gained access to Ledger's npm account, where the packages are distributed. The attackers published malicious versions of the connector kit using the compromised credentials and managed to propagate the drainer malware to dependent applications using this method.
Malware Analysis
Version 1.1.7: This version directly embeds a crypto drainer, a type of malware that executes unauthorized cryptocurrency transactions to transfer assets to attacker-controlled wallets.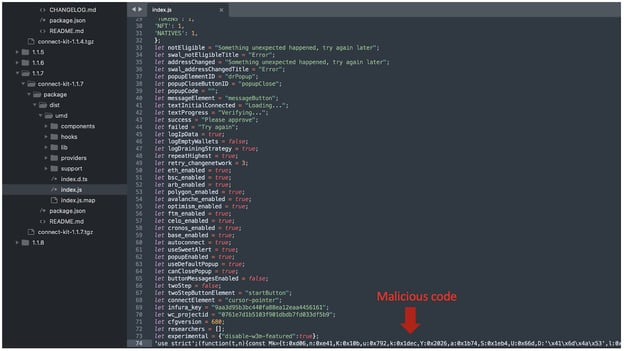
Versions 1.1.5 and 1.1.6: These versions are more insidious. They lack an embedded drainer but instead download a secondary npm package, identified as 2e6d5f64604be31, which acts as a crypto drainer.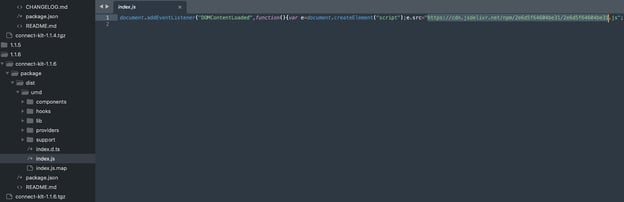
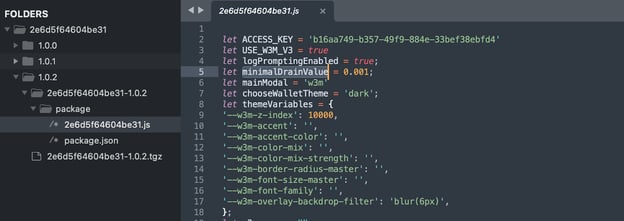
Once installed into your software, the malware presents the users with a fake modal prompt that invites them to connect wallets. Once the users click through this modal, the malware begins draining funds from the connected wallets.
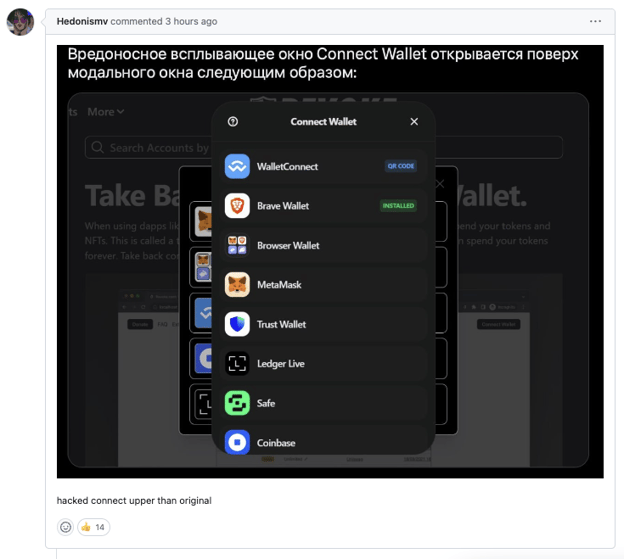
User Hedonismv posted a screenshot of the malware in action on a github issue in the project
So far, within hours of the drainer malware going live, malware has reportedly siphoned over $600,000 in cryptocurrencies from the compromised wallets and counting.
Mitigation and Response
Ledger's response includes the release of a clean npm connect-kit version 1.1.8. A quick upgrade to this version is imperative for all affected parties. If you downloaded the compromised versions, it is important to reinstall the packages at the same version to mitigate the issue.
Continuous monitoring of already-deployed applications' software bill of materials (SBOMs) is recommended to identify any affected applications within your environment.
Why This Matters
This incident underscores the growing trend of software supply chain attacks targeting software development, particularly through open source ecosystems. The complexity and stealth of these attacks make them significant threats.
The specific targeting of cryptocurrency assets demonstrates the evolving tactics of cybercriminals to achieve significant financial gains within hours, directly monetizing their malware.
In our latest State of the Software Supply Chain report, we observed over 245,000 malicious supply chain attacks - a rate which more than doubled in a year, making the scale of software supply chain attacks alarming.
This attack is a critical reminder that developers and organizations must adopt security practices, including regular audits, real-time monitoring, and prompt updates to counter such threats.

Ilkka serves as Field CTO at Sonatype. He is a software engineer with a knack for rapid web-development and cloud computing and with technical experience on multiple levels of the XaaS cake. Ilkka is interested in anything and everything, always striving to learn any relevant skills that help ...
Explore All Posts by Ilkka TurunenTags
